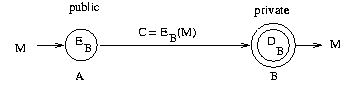4 Public-Key Cryptography
One big disagvantage of the "classical" methods is that before
secret messages can be exchanged the key must have been transferred
over a secure channel.
Public-Key Cryptosystems were introduced in 1977 by Diffie and Hellman.
They use two keys, or algorithms respectively,
say one public key E
and one private key D.
If, for instance, Alice (A) wants to send a message M to Bob (B),
she uses his public key EB to determine
the ciphertext C = EB(M).
Bob receives C, and with the decoding function
DB only known to him he determines DB (C) = DB (EB (M)) = M:
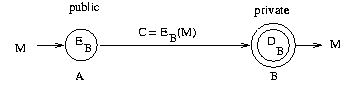
This only works when it is impossible to determine D from E "in
reasonable time". (Theoretically there is the option of encoding all
possible plaintexts M with E and comparing the results
with C.)
The most popular Public-Key algorithms is RSA,
named after its publishers Rivest, Shamir und Adleman.
It relies on the difficulty of factorising large primes.